← zambia go jobs 2025 zambia target to create 1m jobs by 2020 human resource jobs in zambia 2025 human news →
If you are looking for cyber security protection technology background 2275401 Vector Art at you've visit to the right page. We have 35 Pictures about cyber security protection technology background 2275401 Vector Art at like Ai Used In Cybersecurity, Cybersecurity Core Wallpaper, HD Hi-Tech 4K Wallpapers, Images and and also 5 security measures that experts follow (and so should you!) - Panda. Here it is:
Cyber Security Protection Technology Background 2275401 Vector Art At
 www.vecteezy.com
www.vecteezy.com
cyber security protection technology background 2275401 Vector Art at ...
PHP Security : Top Practices For Robust Web Application Defense
 geekpedia.com
geekpedia.com
PHP Security : Top Practices for Robust Web Application Defense
Agent De Sécurité De Magasin - Www.securitsolutions.fr
 www.securitsolutions.fr
www.securitsolutions.fr
Agent de sécurité de magasin - www.securitsolutions.fr
Bolstering Cybersecurity Readiness In The Cloud - Information Age
 www.information-age.com
www.information-age.com
Bolstering cybersecurity readiness in the cloud - Information Age
What Is Cybersecurity? - Forage
 www.theforage.com
www.theforage.com
What Is Cybersecurity? - Forage
Cybersecurity Core Wallpaper, HD Hi-Tech 4K Wallpapers, Images And
 wallpapersden.com
wallpapersden.com
Cybersecurity Core Wallpaper, HD Hi-Tech 4K Wallpapers, Images and ...
Sicurezza Aziendale: Investire Sul Fattore Umano Per Potenziare La
 www.cybersecurity360.it
www.cybersecurity360.it
Sicurezza aziendale: investire sul fattore umano per potenziare la ...
Security And The Right To Security – Gentil Kasongo
 gentilkasongo.com
gentilkasongo.com
Security and the Right to Security – Gentil Kasongo
Cyber Security In Software Development: 12 Outsourcing Tips
 senlainc.com
senlainc.com
Cyber security in software development: 12 outsourcing tips
Security Companies Johannesburg | Complete List 2023
 www.wisemove.co.za
www.wisemove.co.za
Security Companies Johannesburg | Complete List 2023
Closed Padlock On Digital Background, Cyber Security 7812163 Vector Art
 www.vecteezy.com
www.vecteezy.com
Closed Padlock on digital background, cyber security 7812163 Vector Art ...
The Vital Role Of Security Guards - Forester Haynie
 foresterhaynie.com
foresterhaynie.com
The Vital Role of Security Guards - Forester Haynie
The Major Concern Of Every Person Has To Be Their Security - Ivy
 ivycastellanos.com
ivycastellanos.com
The major concern of every person has to be their security - Ivy ...
5 Security Measures That Experts Follow (and So Should You!) - Panda
 www.pandasecurity.com
www.pandasecurity.com
5 security measures that experts follow (and so should you!) - Panda ...
"La Seguridad Al 100% En Internet No Existe"
 www.65ymas.com
www.65ymas.com
"La seguridad al 100% en internet no existe"
The Importance Of Security Training For Employees: A Case Study
 medium.com
medium.com
The Importance of Security Training for Employees: A Case Study ...
Millennials Want The Security Of Their Own Roof Over Their Heads
 www.businessoutreach.in
www.businessoutreach.in
Millennials want the security of their own roof over their heads
Duties And Demand Of Security Guard Services In Los Angeles | CITIGUARD
 www.mysecurityguards.com
www.mysecurityguards.com
Duties and demand of Security guard services in Los Angeles | CITIGUARD
Reviewing The 5 Stages Of The Cybersecurity Lifecycle [+ EXAMPLES
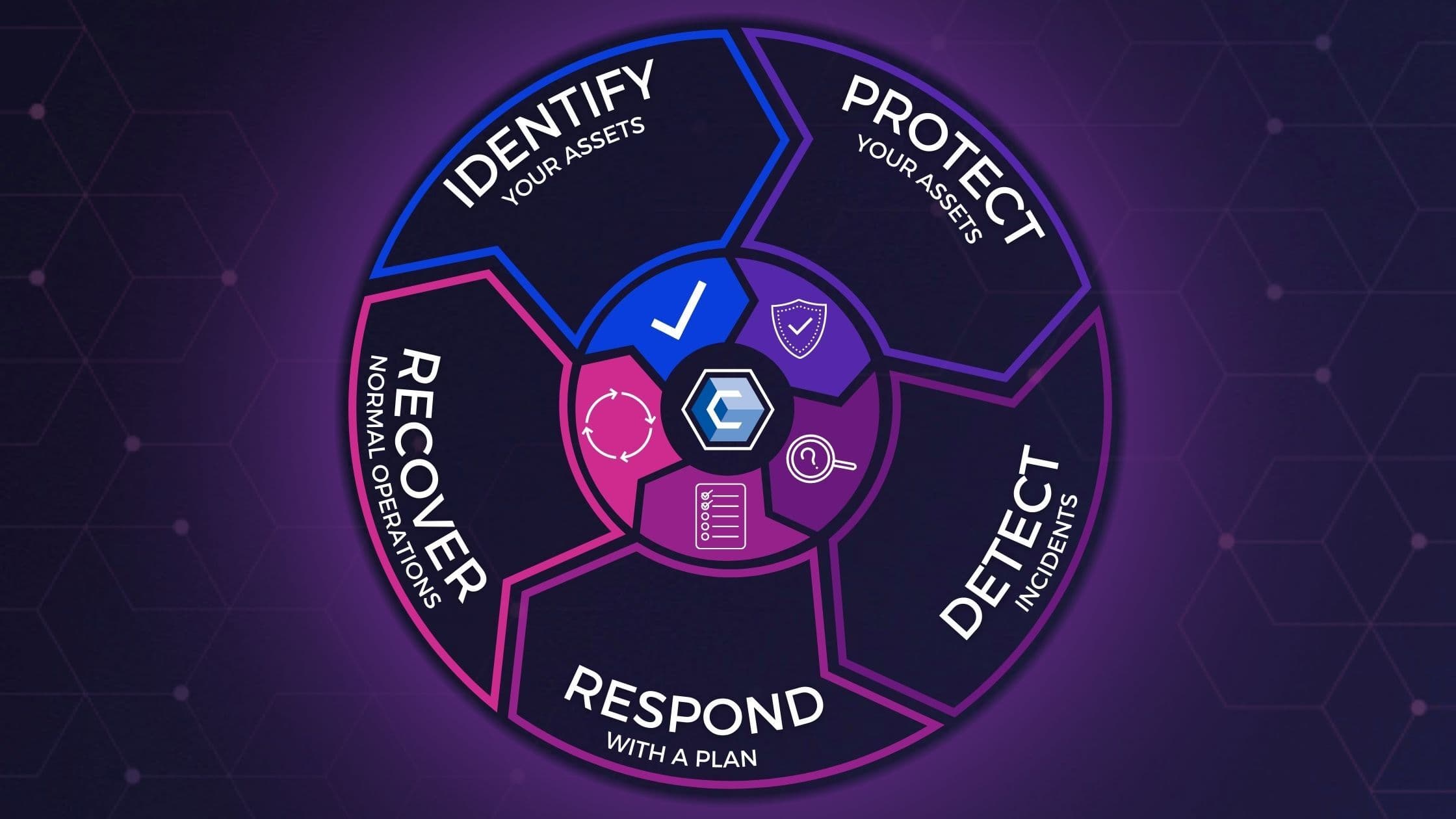 securityboulevard.com
securityboulevard.com
Reviewing the 5 Stages of the Cybersecurity Lifecycle [+ EXAMPLES ...
Seeking Justice For Inadequate Property Security? Learn More!
 keepaustinsafe.com
keepaustinsafe.com
Seeking Justice for Inadequate Property Security? Learn More!
Ai Used In Cybersecurity
 daliminatorxkj1study.z21.web.core.windows.net
daliminatorxkj1study.z21.web.core.windows.net
Ai Used In Cybersecurity
How To Maintain Business Security When You’re Not There? – AtulHost
 www.atulhost.com
www.atulhost.com
How to maintain business security when you’re not there? – AtulHost
Understanding The 3 Phases Of Cybersecurity Architecture | Ardoq
 www.ardoq.com
www.ardoq.com
Understanding the 3 Phases of Cybersecurity Architecture | Ardoq
Desain Arsitektur Keamanan - Azure Architecture Center | Microsoft Learn
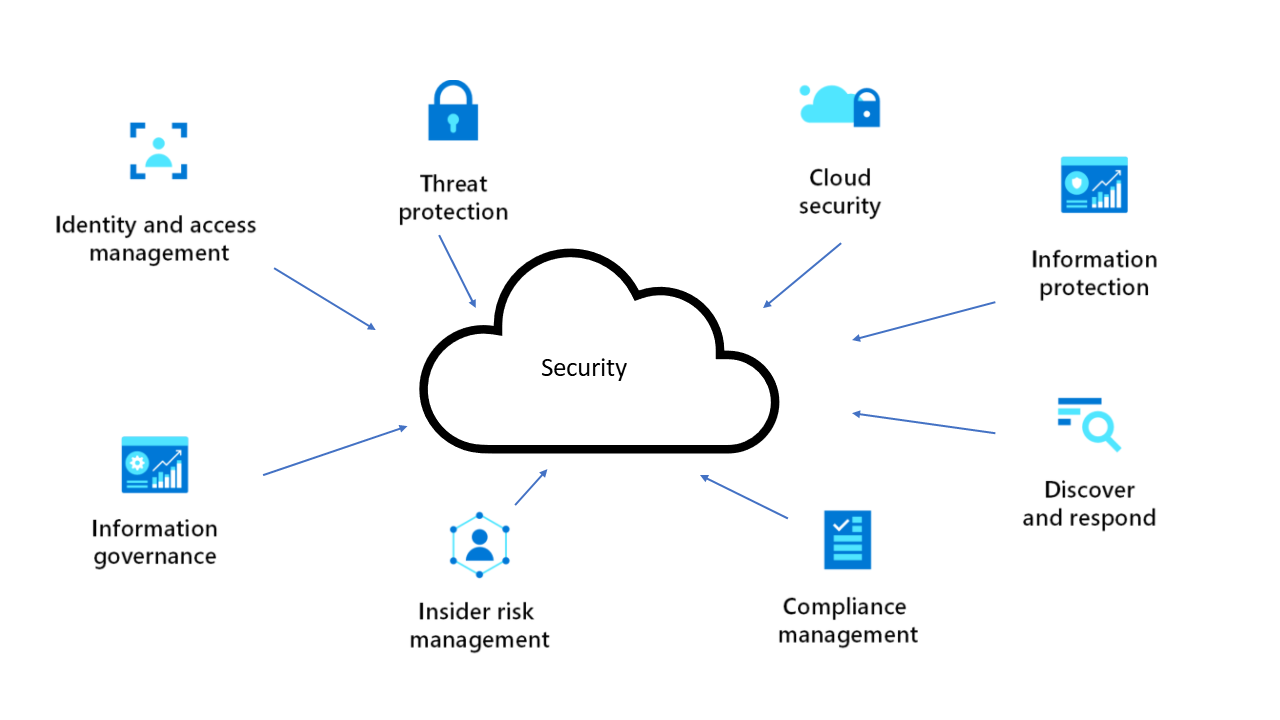 learn.microsoft.com
learn.microsoft.com
Desain arsitektur keamanan - Azure Architecture Center | Microsoft Learn
Innovations And Breakthroughs From Nigerian Security Scholars
 disciplines.ng
disciplines.ng
Innovations and Breakthroughs from Nigerian Security Scholars
Security Guard Images
 ar.inspiredpencil.com
ar.inspiredpencil.com
Security Guard Images
There Is A New Focus On Physical Security And Cyber Security Convergence
 www.grcviewpoint.com
www.grcviewpoint.com
There Is A New Focus on Physical Security and Cyber Security Convergence
ISO/IEC 27032:2023—Cybersecurity Guidelines - ANSI Blog
 blog.ansi.org
blog.ansi.org
ISO/IEC 27032:2023—Cybersecurity Guidelines - ANSI Blog
The Top Five Cybersecurity Trends In 2023
 www.forbes.com
www.forbes.com
The Top Five Cybersecurity Trends In 2023
Security Considerations For Deploying Notes Plugins
 www.bcchub.com
www.bcchub.com
Security Considerations for Deploying Notes Plugins
Professional Security Services In Punjab And India | Manpower
 mpmp.in
mpmp.in
Professional Security Services in Punjab and India | Manpower ...
Aimssoft.com
 www.aimssoft.com.hk
www.aimssoft.com.hk
aimssoft.com
Cybersecurity: The Forever Problem
 jpt.spe.org
jpt.spe.org
Cybersecurity: The Forever Problem
5 Contoh Surat Lamaran Kerja Security/Satpam Lengkap Dan Cara
 www.cakeresume.com
www.cakeresume.com
5 Contoh Surat Lamaran Kerja Security/Satpam Lengkap dan Cara ...
Cyber Security: Saiba O Que Faz Um Profissional De Cibersegurança
 dciber.org
dciber.org
Cyber Security: saiba o que faz um profissional de cibersegurança
5 contoh surat lamaran kerja security/satpam lengkap dan cara .... The top five cybersecurity trends in 2023. 5 security measures that experts follow (and so should you!)